cyber threat intelligence and incident response are not mere buzzwords but pillars of defense. Let's dissect these concepts to understand their significance and synergy. Imagine a scenario where a large financial institution is targeted by a group of hackers who have gained access to the company's network. The hackers have stolen sensitive customer data, including personal and financial information. The company's incident response team is alerted to the breach and begins to investigate. However, they quickly realize that the hackers use advanced techniques to evade detection and cover their tracks. The team is overwhelmed and struggling to keep up with the attackers. This is where cyber threat intelligence (CTI) comes in. By analyzing extensive data, CTI can uncover patterns, vulnerabilities, and techniques used by attackers. This deep dive into data transforms into actionable insights, enabling organizations to stay ahead of potential threats. CTI can provide the incident response team with a deeper understanding of the attack, including its origins, motives, and methods, which can be used to improve incident response and prevent similar attacks in the future. In this scenario, CTI can help the incident response team identify the most critical systems and data, prioritize response efforts, and determine the best course of action for containing and remedying the attack.
Contents list ⮛
- ➣ Cyber Threat Landscape (Learn how Cyber threats have evolved over the years and their types)
- ➣ Role of Cyber Threat Intelligence (Basic Concept of CTI, Tools that provide CTI, and how organizations can gather CTI from different sources)
- ➣ Building a Proactive Incident Response (Key elements of an incident response plan, strategies for detecting cyber threats in real-time, and some real-world examples of successful incident response efforts)
- ➣ Human Element in Cybersecurity (Learn about how to protect digital assets, Training and awareness essentials, and the culture of cybersecurity)
- ➣ Future Of Cyber Threat Intelligence (See how AI and Machine learning are enhancing the threat detection, analysis, and response in the Cyber threat intelligence landscape)
1-The Cyber Threat Landscape
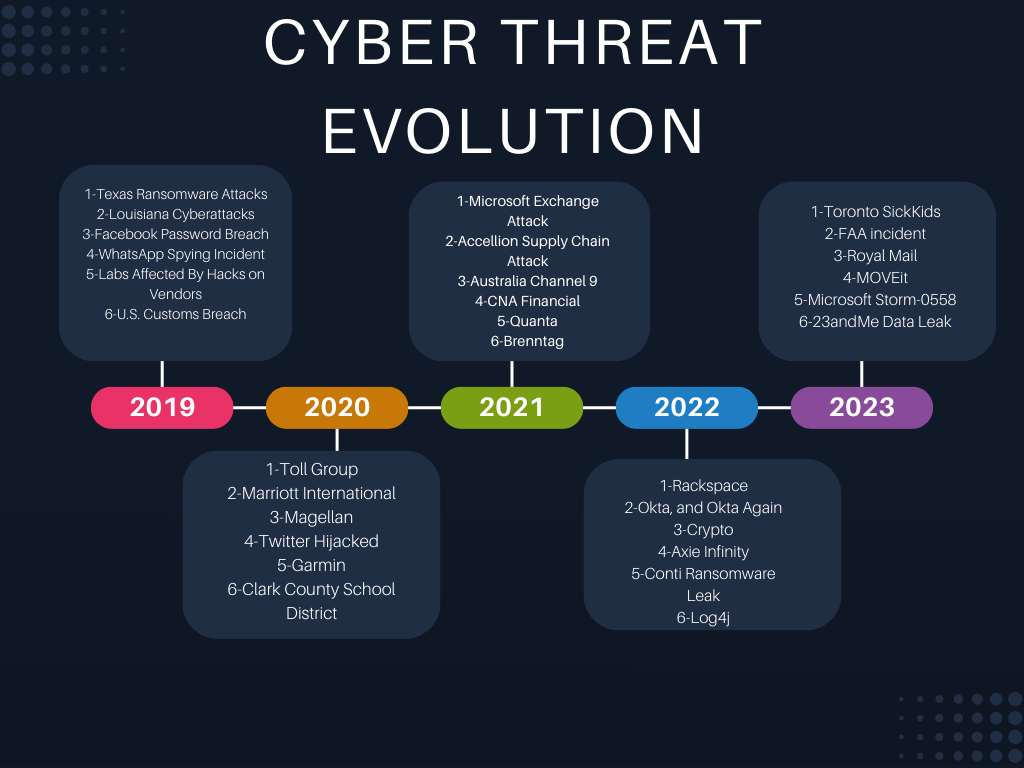
Evolution Of Cyber Threat Landscape:
The evolution of cyber threats over the years has been marked by a rapid increase in sophistication and diversity. Attackers have become more advanced, leveraging new technologies such as artificial intelligence to develop more sophisticated methods. The threat landscape has been influenced by factors such as the increasing reliance on information technology products and services, the rise of the dark web, and the greater availability of skills, personnel, and finances to drive cyber-attacks. Some of the prominent threats include ransomware, malware, social engineering, threats against data and availability, disinformation, and supply chain targeting. The cyber threat landscape has also seen a shift towards quieter attacks, such as crypto-jacking and IoT malware. The evolving threat landscape underscores the critical importance of robust cybersecurity measures and the need for organizations to remain vigilant and adaptable in the face of ever-changing cyber threats.
Types Of Cyber Threats:
The types of cyber threats include various malicious activities and attacks aimed at compromising computer systems and networks. Some common types of cyber threats are:
- Malware: Malicious software designed to damage or gain unauthorized access to a computer system.
- Ransomware: A type of malware that encrypts a victim's files and demands a ransom for their release.
- Distributed Denial of Service (DDoS) Attacks: Overwhelming a system with traffic to make it unavailable.
- Phishing: Deceptive attempts to obtain sensitive information, often through fraudulent emails or websites.
- Man-in-the-Middle (MITM) Attacks: Interception and potential alteration of communication between two parties.
- Social Engineering: Manipulating individuals to divulge confidential information or perform actions.
- Insider Threats: Malicious activities or security breaches caused by individuals within an organization.
- Supply Chain Attacks: Compromising a company's products or services through its supply chain.
- Identity-Based Attacks: Unauthorized access to systems or data using stolen or forged credentials.
- Code Injection Attacks: Inserting malicious code into a computer program.
These threats pose significant risks to organizations and individuals, highlighting the importance of robust cybersecurity measures and awareness.
2-Role Of Cyber Threat Intelligence (CTI)
What is CTI:
Cyber threat intelligence (CTI) is knowledge, skills, and experience-based information concerning the occurrence and assessment of both cyber and physical threats and threat actors. It is intended to help mitigate potential attacks and harmful events. CTI sources include open-source intelligence, social media intelligence, human intelligence, technical intelligence, device log files, forensically acquired data, or intelligence from internet traffic and data derived from the deep web. CTI provides several benefits, including the ability to develop a proactive and robust cybersecurity posture, drive momentum toward a predictive cybersecurity posture, provide context and insights about active attacks and potential threats to aid decision-making, prevent data breaches, and reduce costs. CTI is vital in modern cybersecurity as it empowers organizations to make informed decisions, reduce the risk of cyber-attacks, improve security defenses, and respond to incidents more effectively. It is a multidimensional resource that sheds light on the identity and motives of potential threat actors, enabling organizations to predict, prevent, and mitigate cyber threats, ultimately safeguarding against potential attacks and ensuring robust security measures that align with organizational objectives.
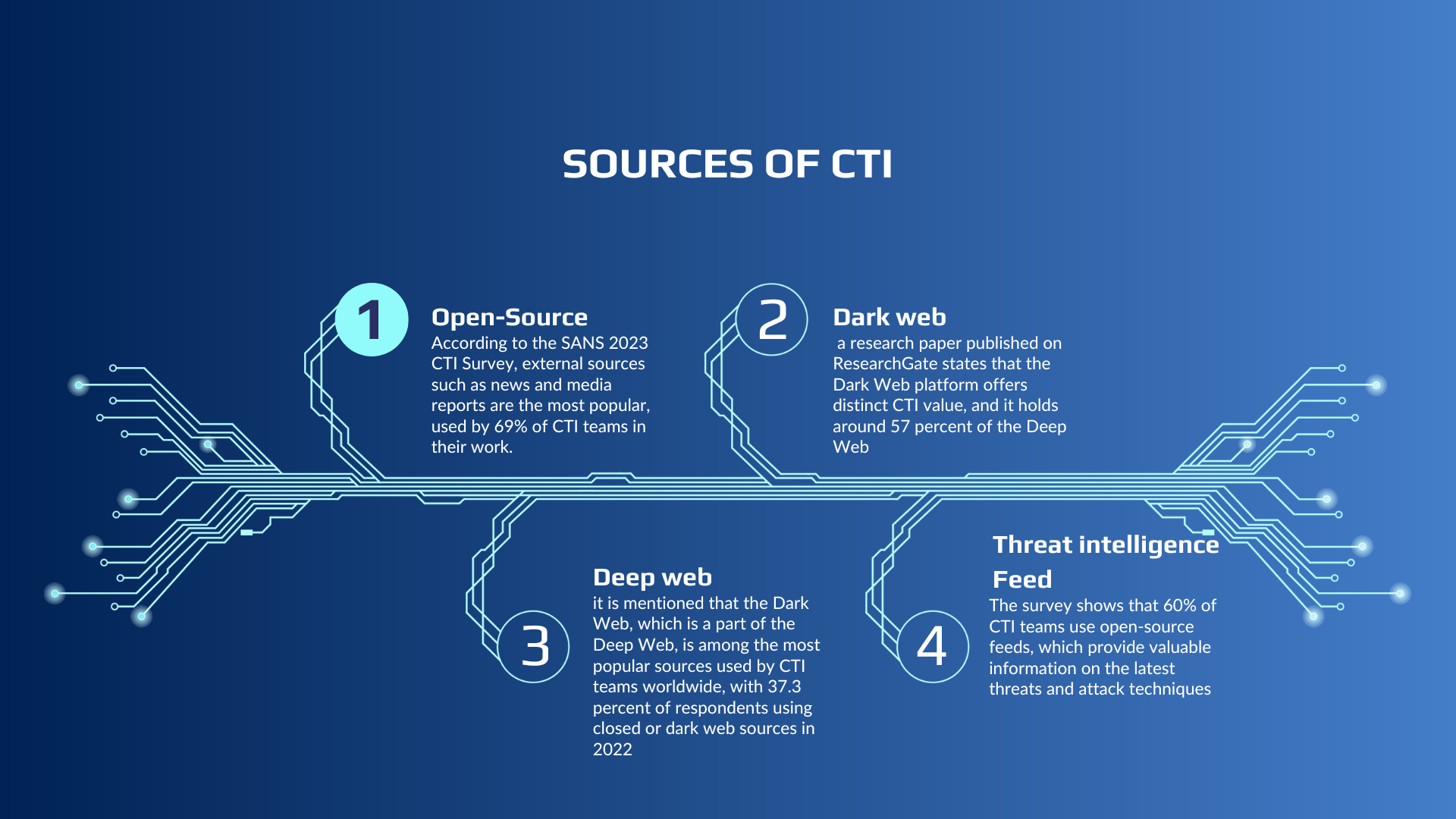
Sources of CTI:
Organizations can gather cyber threat intelligence (CTI) from various sources, including:
Open-Source Intelligence: This includes information from publicly available sources such as blogs, news reports, public block lists, and private or commercial sources like vendors of threat intelligence software. Some open-source threat intelligence sources are:
- Cybersecurity and Infrastructure Security Agency (CISA) News and Events
- Red Canary
- SANS Internet Storm Center
- And many more
Dark Web: This refers to content accessible only through the use of specialized software, configurations, or authorization. Threat actors sell information on dark web forums and marketplaces, providing valuable threat intelligence such as leaked information, threat campaigns, and malicious technologies, like malware and ransomware.
Deep Web: This includes websites, databases, and files that conventional search engines cannot index, such as content behind login pages and paywalls.
Threat Intelligence Feeds: These feeds provide information on various cyber threats, including leaked data, threat campaigns, malicious technologies, and more. Some of the top cyber threat intelligence feeds can be found in.
By gathering CTI from these sources, organizations can develop a proactive and robust cybersecurity posture, drive momentum toward a predictive cybersecurity posture, provide context and insights about active attacks and potential threats to aid decision-making, prevent data breaches, and reduce costs.
CTI Tools and Platforms:
There are several key tools and platforms that aid in collecting and analyzing cyber threat intelligence (CTI). Some of these tools include:
- CISA Automated Indicator Sharing (AIS) Threat Intelligence Feed: Provides machine-readable cyber threat indicators and defensive measures.
- Blocklist.de Threat Intelligence Feed: A free feed run by volunteers that provides indicators of compromise and other threat information.
- Talos Intelligence Feed: Offers real-time threat intelligence and protection against new and emerging threats.
- AlienVault OTX Threat Intelligence Feed: Allows security teams to share threat intelligence, integrate with existing workflows, and automatically block command and control servers (CC&C) domains.
- Spamhaus Threat Intelligence Feed: Focuses on email threats, providing real-time information on new phishing campaigns and malicious email senders.
- CrowdSec Threat Intelligence Feeds: Offers community-driven threat intelligence, enabling organizations to share threat data and benefit from a larger pool of knowledge.
- Cyber Cure Threat Intelligence Feeds: Provides actionable threat intelligence, enabling organizations to detect and prevent advanced malware and cyber threats.
- Cyber Threat Alliance (CTA): A threat intelligence sharing platform that enables organizations to share and analyze threat data in real-time.
- Cybersecurity and Infrastructure Security Agency (CISA): Provides resources, tools, and services that help organizations improve their cybersecurity posture and respond to threats.
These tools and platforms help organizations gather, analyze, and share threat intelligence, enabling them to detect and respond to cyber threats more effectively. By leveraging these resources, organizations can improve their security effectiveness and better protect their networks and systems from evolving cyber threats.
3- Building a Proactive Incident Response Plan
Components Of Incident Response:
The key elements of a robust incident response plan include:
- Preparation: Advance preparation, including using risk assessments to bolster resiliency in networks, systems, applications, and devices, defining the roles and responsibilities of individuals on the incident response team, and preparing incident response communication channels.
- Detection and Analysis: The ability to detect and analyze potential security incidents to determine their severity and prioritize the response. This phase involves identifying the nature and scope of the incident.
- Containment, Eradication, and Recovery: Once an incident is detected and analyzed, the next step is to contain the incident to prevent further damage, eradicate the threat, and recover from the incident. This involves isolating affected systems, removing the threat, and restoring normal operations.
- Lessons Learned and Ongoing Improvement: After an incident, it's important to conduct a post-incident analysis to assess the attack's impact, identify lessons learned, and use that information to improve the organization's security posture. This phase also involves strategizing improvements and ongoing security enhancements.
- Formal Documentation of Roles and Responsibilities: Clearly defined roles and responsibilities for the incident response team, including an incident response manager, security analysts, engineers, and threat researchers.
- Incident Response Threshold Determination: Defining the criteria for when an incident is declared, ensuring that the response is appropriately prioritized.
- Processes for Mitigation and Containment: Establishing processes for managing and containing incidents effectively, such as isolating impacted resources, setting up a central communications hub, and other strategies.
- Incident Response Plan: Formal documentation describing incident response procedures, covering the entire incident response process, including preparation, detection, analysis, containment, eradication, recovery, and post-incident analysis.
These elements are essential for organizations to effectively prepare for, detect, respond to, and recover from security incidents.
Real-Time Threat Detection:
Real-time threat detection involves the use of advanced technologies and strategies to identify potential cyber threats as they occur. Some strategies for detecting cyber threats in real-time include:
- Behavioral Modeling: Security tools can create a log of different files, geolocation, and requested resources to model the behavior of known cyber threats.
- Proactive Threat Hunting: Real-time threat detection doesn't just wait for cybersecurity threats; it proactively seeks out security risks that may not be known yet. This involves systematic analysis of the entire network, assessing every asset, resource, endpoint, URL, and hardware for potential security risks.
- Threat Intelligence Feeds: These feeds provide real-time information on new and emerging threats, enabling organizations to stay ahead of potential attacks. They can identify infrastructure used by attackers, such as command-and-control servers, phishing websites, or payment processors, and disrupt their operations.
- Continuous Monitoring: Organizations can continuously monitor network activity, including dedicated tools, to ensure their systems are safe.
- Threat Hunting: This involves security analysts actively going into their network, endpoints, and security technology to look for threats or attackers that may be lurking as yet undetected. This is an advanced technique generally performed by veteran security and threat analysts.
By employing these strategies, organizations can enhance their ability to detect and respond to cyber threats in real time, ultimately strengthening their overall cybersecurity posture.
Case Studies:
Here are some real-world examples of successful incident response efforts:
- Successful Incident Response with the Help of a Security Operations Center: In this case study, a Security Operations Center (SOC) played a critical role in facilitating a comprehensive response strategy, adherence to legal and regulatory obligations, and seamless communication throughout the incident response process. The SOC team collaborated closely with the organization's incident response team, IT department, legal counsel, and other stakeholders to contain the incident, remediate the issue, and restore affected systems (Read More).
- Top 15 Incident Response Use Cases: This article highlights the importance of having a robust incident response plan by exploring the top incident response use cases. These use cases include network traffic analysis, cloud security, web application security, mobile device security, and more. By having a comprehensive incident response plan, organizations can mitigate the negative impacts of an incident, limit damage, and help the organization survive turbulence after a data breach or cyberattack (Read More).
- 7 Phases of Incident Response: Essential Steps for a Comprehensive Response Plan: This article outlines the seven phases of incident response, including preparation, identification, containment, eradication, recovery, lessons learned, and ongoing improvement. By following these phases, organizations can effectively address cyber threats and strengthen their cybersecurity posture (Read More).
These examples demonstrate the importance of having a comprehensive incident response plan, including a Security Operations Center, collaboration between teams, and a structured approach to incident response. By having a robust incident response plan, organizations can mitigate the negative impacts of an incident, limit damage, and improve their overall cybersecurity posture.
4- Human Element in Cybersecurity
Training and Awareness:
Educating employees and stakeholders about cybersecurity is crucial for organizations to protect their digital assets and maintain a secure environment. Here are some reasons why training and awareness are essential:
- Employee-driven security: Employees are often the first line of defense against cyber threats, making it essential for them to understand potential risks and how to mitigate them. By providing cybersecurity training, organizations can equip their employees with the knowledge and skills needed to identify and respond to potential threats.
- Reducing human error: Many cyber threats, such as phishing attacks, rely on human error for success. Educating employees about common threats and best practices can help reduce the likelihood of falling victim to these attacks.
- Compliance with regulations: Organizations must comply with various data protection regulations, and providing cybersecurity training to employees can help ensure that they are adhering to these rules and avoiding costly fines.
- Protecting organizational assets: A well-informed workforce is more likely to prioritize cybersecurity and take appropriate measures to protect the organization's digital assets, such as implementing strong access controls and reporting potential security incidents.
- Adapting to the evolving threat landscape: As cyber threats evolve; employees and stakeholders need to stay informed about the latest trends and best practices. Regular cybersecurity training can help organizations adapt to the changing landscape and remain resilient against new and emerging threats.
Some examples of successful cybersecurity awareness programs include the CISA Cybersecurity Awareness Program, which aims to increase understanding of cyber threats and empower individuals to protect themselves and their organizations, and KnowBe4. This platform offers security awareness training and simulated phishing attacks to help organizations manage IT security problems related to social engineering, spear phishing, and ransomware attacks. By investing in cybersecurity training and awareness, organizations can better protect their digital assets, reduce the risk of cyber-attacks, and improve their overall cybersecurity posture.
Creating a Cybersecurity Culture:
Creating a cybersecurity culture is essential for organizations to protect their digital assets and maintain a secure environment. Building a culture of cybersecurity involves the following key elements:
- Leadership and management commitment: Leaders and management must prioritize cybersecurity, allocate resources, and demonstrate their commitment to security initiatives. They should lead by example.
- Employee engagement: Fostering a cybersecurity culture requires the collective efforts of every individual in the organization. Emphasizing awareness, education, and engagement can help create a resilient fortress against cyber threats.
- Making security relatable: Starting in the C-suite and making security relatable to employees is crucial for building a cybersecurity culture. This involves understanding stakeholders' behaviors and challenges and creating security culture initiatives tailored to their needs.
- Gamification and fun learning: Role-playing scenarios and gamification can make cybersecurity training more enjoyable and engaging, helping employees better understand the risks and their role in security.
- Rewarding good security behavior: Celebrating and rewarding employees who exemplify exemplary security practices can be a powerful motivator. By acknowledging employees who demonstrate vigilance and proactive action, organizations reinforce the value of cybersecurity.
- Continuous improvement: Encouraging a culture of continuous improvement by learning from security incidents and staying up to date with the latest cybersecurity trends can help organizations build a strong cybersecurity culture.
- Responsibility and accountability: Assigning specific individuals the responsibility of maintaining and promoting cybersecurity within the organization can help ensure that everyone understands their role in security and feels empowered to take action.
By incorporating these elements into an organization's culture, companies can create a strong cybersecurity culture that effectively protects their digital assets, data, and systems from cyber threats.
5- Best Practices and Tips
Continuous Monitoring:
Continuous monitoring is essential for organizations to stay ahead of evolving cyber threats. Here are some reasons why ongoing monitoring is crucial:
- Proactive Approach: Continuous monitoring allows organizations to transition from a reactive to a proactive cybersecurity stance. By regularly examining and assessing their security measures, organizations can identify vulnerabilities and address them before intruders exploit them.
- Adapting to the Evolving Threat Landscape: The cyber threat landscape is constantly changing, with new threats and attack methods emerging regularly. Continuous monitoring enables organizations to stay informed about the latest trends and adapt their security measures accordingly.
- Streamlined Compliance: Ongoing monitoring helps organizations maintain compliance with data protection regulations by regularly reviewing and updating their risk management strategies and ensuring that implemented controls are effective.
- Improved Incident Response: Continuous monitoring can help organizations detect security incidents earlier, allowing them to respond more quickly and effectively to minimize the impact of an attack.
- Enhanced Threat Intelligence: Modern continuous cyber risk monitoring solutions often integrate with global threat intelligence feeds, enabling organizations to compare their environment with the latest threat data and shield themselves from even the most recent cyber threats.
- Cost-Effective: Continuous monitoring can help organizations identify potential threats and vulnerabilities before they escalate into full-blown security incidents, saving them time and money in the long run.
By investing in continuous monitoring, organizations can effectively protect their digital assets, maintain a secure environment, and stay ahead of evolving cyber threats.
Collaboration and Information Sharing:
Collaboration and information sharing are crucial for addressing cyber threats effectively. By working together and sharing valuable information, organizations, governments, and security professionals can enhance their cybersecurity readiness and improve security measures. Here are some reasons why collaboration and information sharing are essential:
- Improved threat intelligence: Sharing information about cyber threats, such as indicators of compromise, threat reports, and analysis of emerging threats, enables organizations to better understand and respond to potential attacks.
- Enhanced situational awareness: Collaboration allows organizations to gain insights into the current cyber threat landscape, helping them stay informed about the latest trends and adapt their security measures accordingly.
- Efficient use of resources: By pooling resources and information, organizations can leverage each other's efforts and shared data most cost-effectively, leading to better analysis of security data.
- Faster response times: Rapid information sharing can help organizations detect and respond to security incidents more quickly, minimizing the impact of an attack.
- Public-private partnerships: Collaboration between public and private sectors is essential for addressing cyber threats effectively. By working together, organizations and governments can share valuable information and resources, enabling them to better protect their digital assets and maintain a secure environment.
- Building trust and rapport: Collaboration fosters trust and rapport among organizations, enabling them to share threat intelligence and best practices more effectively.
However, there are also challenges associated with collaboration and information sharing, such as the potential increase in the risk of data breaches and the need to prioritize the sharing of only the most critical information. To strike a balance, organizations must ensure that they have robust cybersecurity measures in place, prioritize sharing only the most critical information, build trust, streamline processes for quick responses, and take personal responsibility.
By fostering collaboration and information sharing within the cybersecurity community, organizations can effectively protect their digital assets, maintain a secure environment, and stay ahead of evolving cyber threats.
6- Future Of Cyber Threat Intelligence
AI and Machine Learning:
Artificial Intelligence (AI) and Machine Learning (ML) are revolutionizing Cyber Threat Intelligence (CTI) by enhancing threat detection, analysis, and response. Advanced machine learning algorithms empower AI systems to sift through extensive data volumes, pinpoint patterns, and accurately spot potential threats. These systems maintain continuous vigilance over network traffic, endpoint behaviors, and user activities to detect anomalies and potential security breaches. By harnessing machine learning algorithms, AI conducts in-depth analyses of extensive data from various sources, including historical incidents, network logs, user behaviors, and threat intelligence feeds, enabling AI-driven systems to unearth patterns, and correlations, and provide real-time threat intelligence. AI and ML also play a crucial role in threat analysis, helping cybersecurity professionals understand the nature of cyber threats, their origins, and potential impacts. ML models continuously learn from new data, making them more effective over time and adapting to the evolving threat landscape. AI and ML are transforming how organizations produce and curate cyber threat intelligence, enabling them to proactively defend against malicious threats and bolster their defenses. Therefore, AI and ML are reshaping the future of CTI by providing organizations with enhanced threat detection, proactive threat mitigation, and intelligent automation, ultimately empowering them to maintain a proactive stance against cyber threats in an ever-evolving security landscape.
Adapting to New Threats:
Staying ahead in a constantly changing landscape requires a comprehensive approach that encompasses understanding the competitive landscape, identifying your competitive advantage, setting clear goals and objectives, conducting market research, and developing a unique value proposition. It is essential to adapt to changing market conditions, stay updated on industry trends, and invest in research and development initiatives. Additionally, managing risk, staying informed about the latest technology trends, and embracing innovation and experimentation are vital strategies for staying ahead.
Furthermore, it is important to anticipate change, bring in external perspectives, and invest in resources and networks to bring fresh insights from the outside world. Finally, staying relevant in a rapidly changing business landscape involves investing in the growth and development of your employees. By adopting these approaches, organizations can thrive in dynamic environments and seize new opportunities for growth and innovation. The strategies for staying ahead in a constantly changing landscape include:
- Understanding the competitive landscape and identifying competitive advantage.
- Adapting to changing market conditions and staying updated on industry trends.
- Conducting market research and investing in research and development initiatives.
- Managing risk and embracing innovation and experimentation.
- Anticipating change, bringing in external perspectives, and investing in resources and networks.
- Staying informed about the latest technology trends and investing in the growth and development of employees.
These strategies provide a roadmap for businesses to navigate dynamic environments and achieve success.
Wrapped Up
As we navigate the digital age, embracing the realms of cyber threat intelligence and incident response is not an option but a necessity. By staying informed, adopting proactive strategies, and learning from experiences, we fortify our digital landscapes against the ever-persistent tide of cyber threats. By employing these strategies, organizations can enhance their cyber resiliency and adapt to the ever-changing cybersecurity landscape, ensuring that they remain secure and resilient against evolving cyber threats. We encourage you to share your thoughts, questions, and experiences to foster further engagement and collaboration in this critical area.